Did you know that you can stop your users from logging into any of your Azure or Office365 resources based on the location they are in? What about the types of devices that they can connect from or only allowing connections that use MFA? These things are all possible to restrict.
This seriously limits the attack surface and also helps to stop compromised devices and accounts from being used.
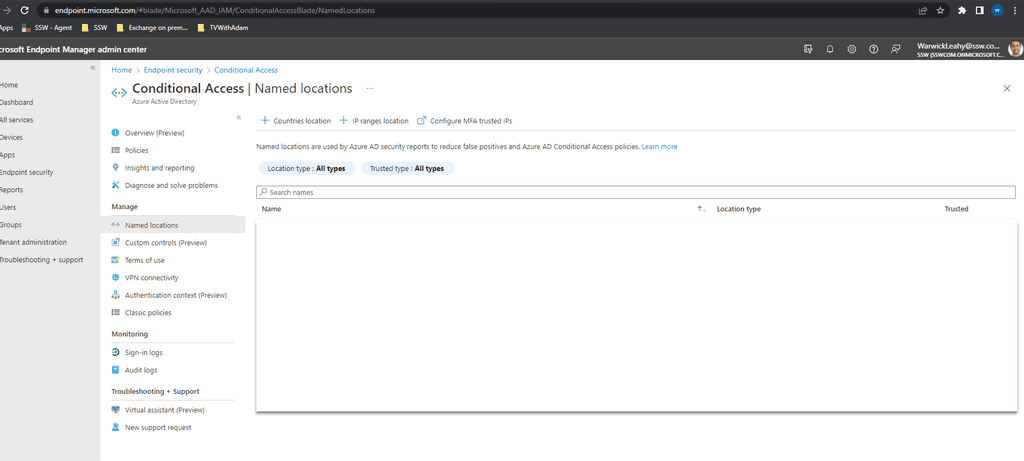
Configure locations
First you need to add any locations that you require for your office.
- Go to https://endpoint.microsoft.com | Endpoint security | Conditional Access | Named locations
-
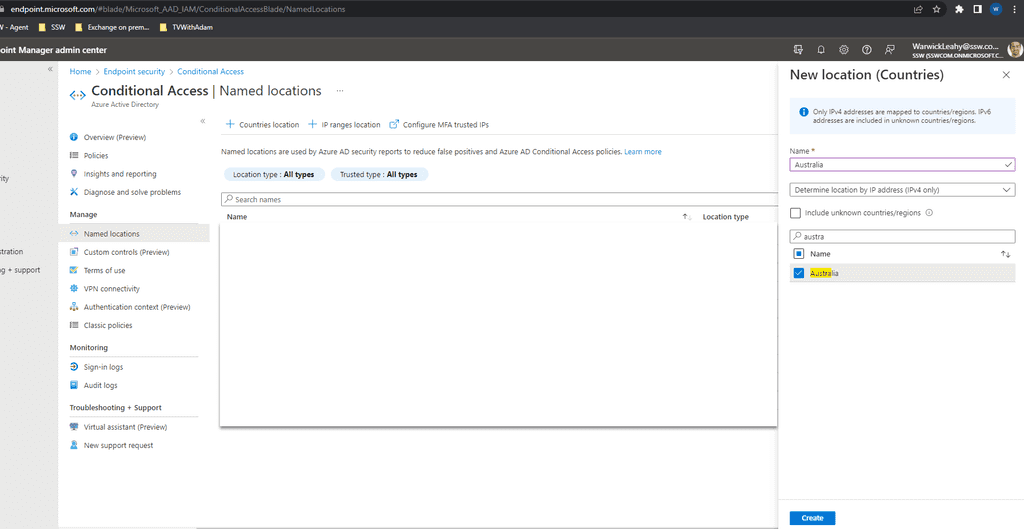
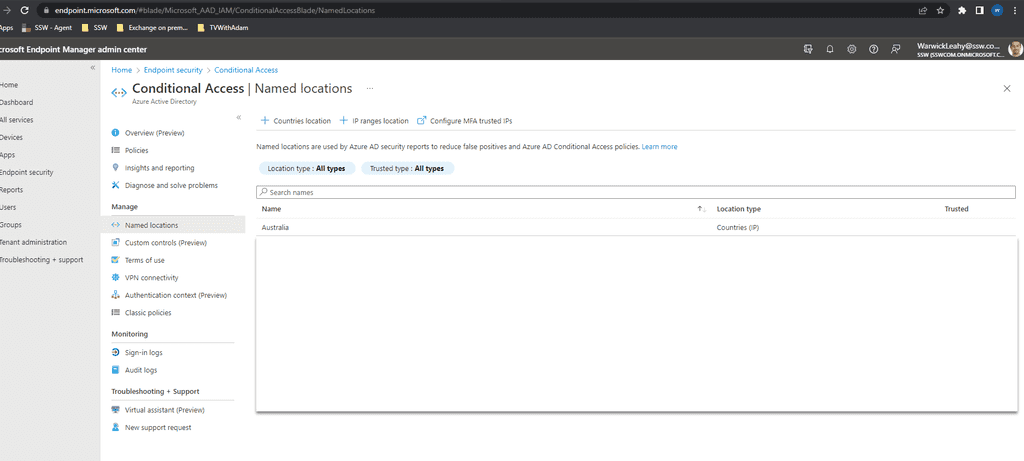
Click + Countries location and add required countries
-
Add as many as you require for your users to access
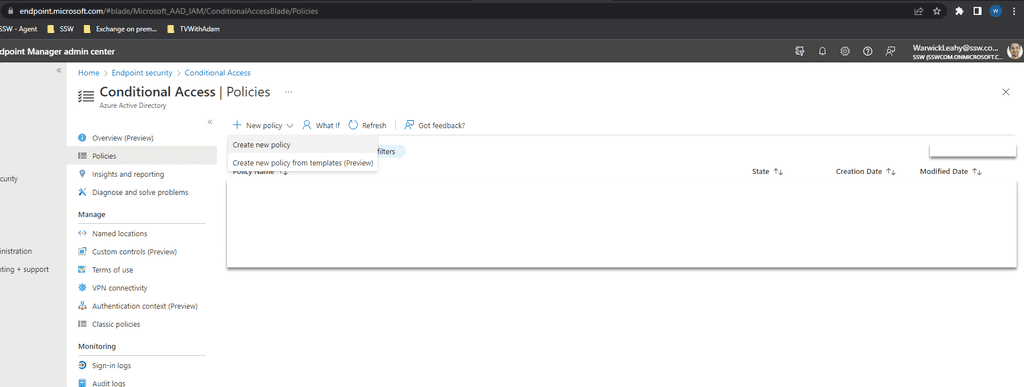
Configure policies
Now configure some policies to implement these rules
- Go to https://endpoint.microsoft.com | Endpoint security | Conditional Access | Policies
-
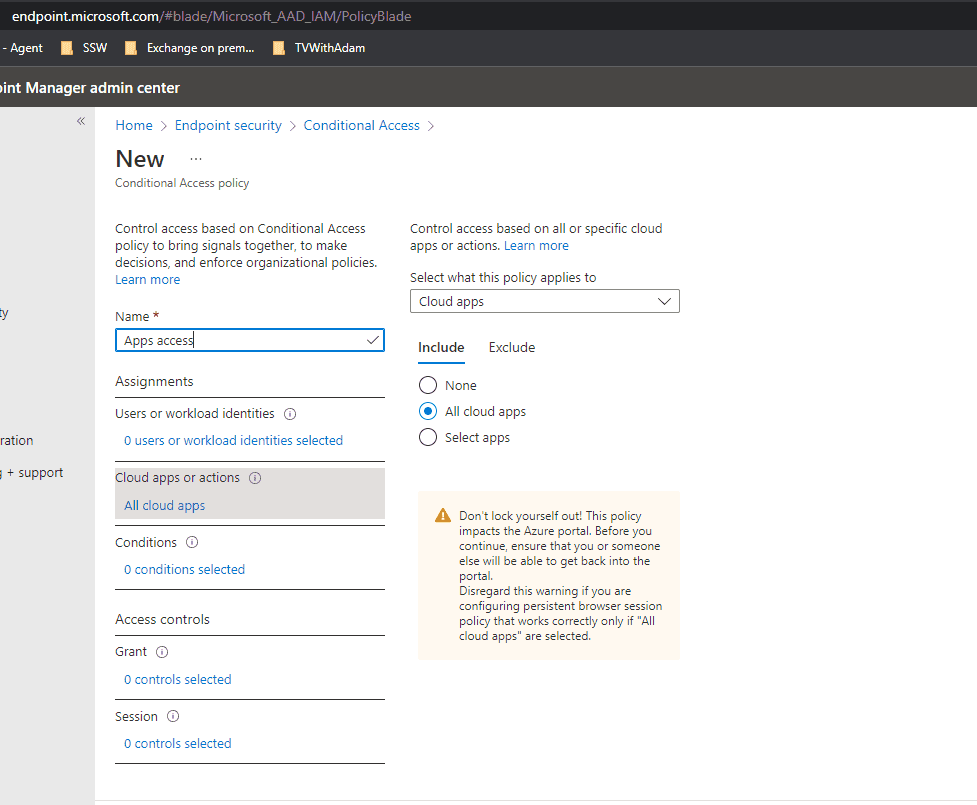
Select New policy | Create new policy
-
Give it a name then select Cloud apps or actions | Select All cloud apps
-
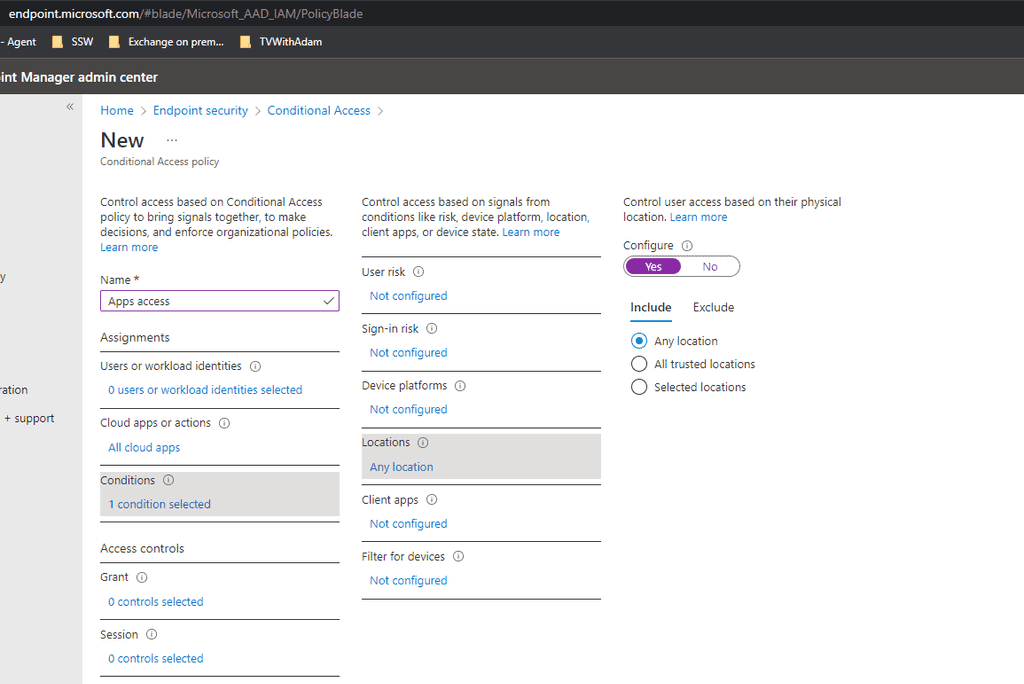
Select Conditions | Locations Then set configure to yes and Include to "Any location"
-
On Exclude choose Selected locations and then exclude your workers countries (i.e. Australia)
Note: This must be done this way as the user must not meet a block access rule ever if they are to login.
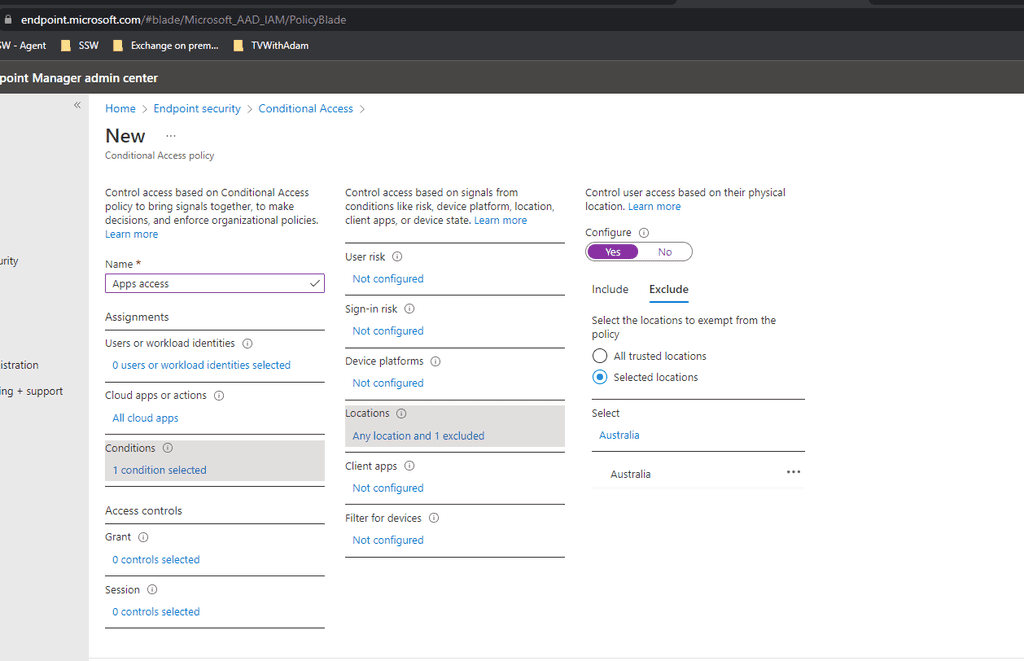
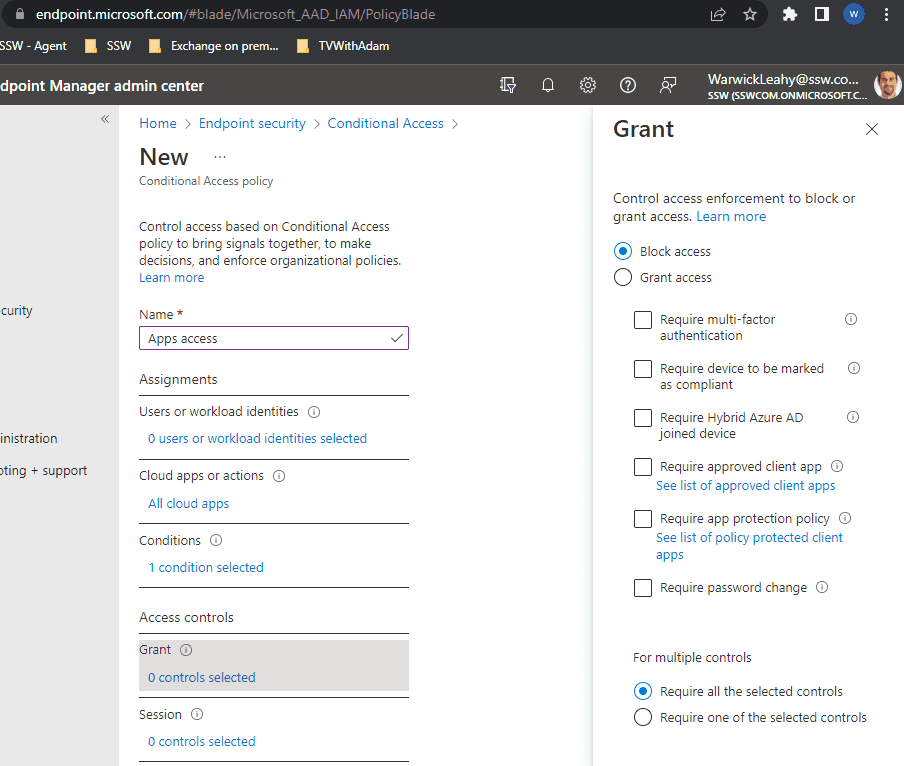
Create a grant rule
- Similarly create a rule that applies to all cloud apps as above
-
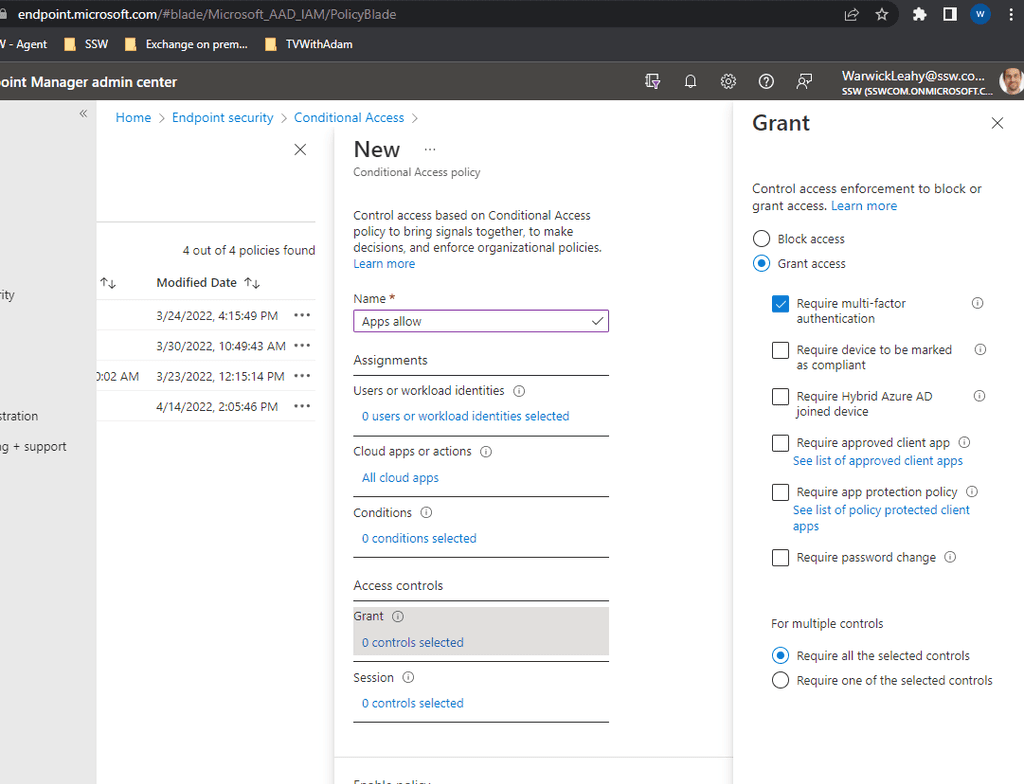
This will be exactly the same as the above rule except that you should not have conditions and should Grant access with MFA
-
You will notice that each of these rules have a 'Report only' mode or enforce. You should leave it on report mode and monitor the audit logs.
Check for any failures and only apply the rules to a small subset of your users before changing them to 'On'. This is very important as you can stop everyone including yourself from logging in.
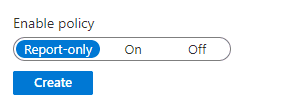
Figure: Choose report only until you are sure that your rules work
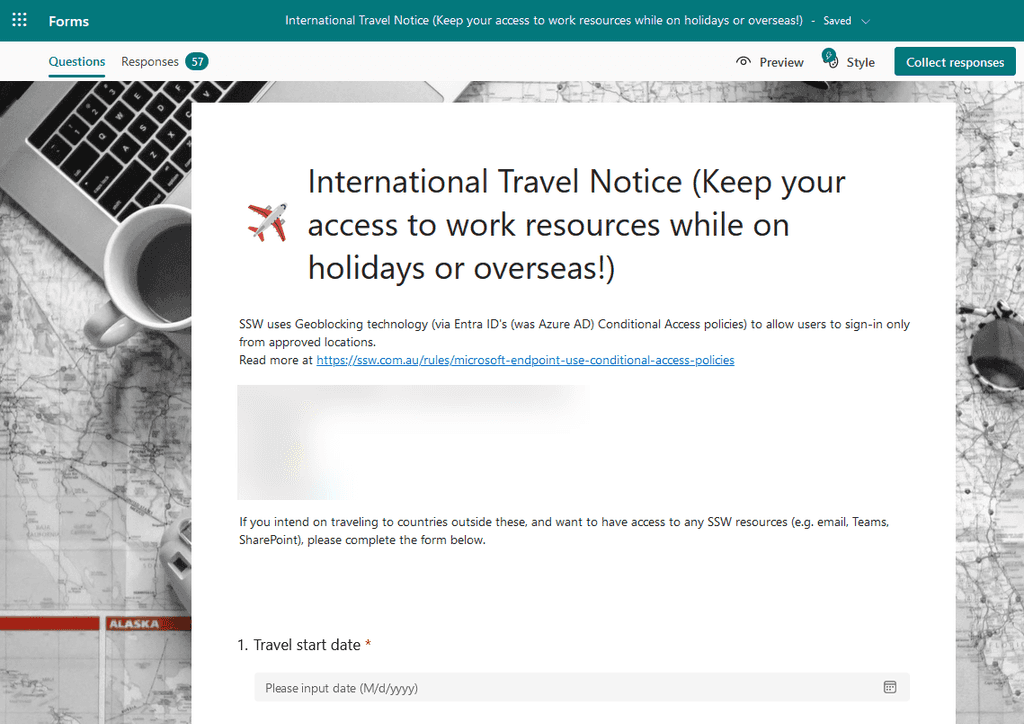
International Travel Notice - Exclude travelling users and let them keep their access to work resources while on holidays or overseas
When a user goes overseas and needs access to the company resources, you should temporarily exclude them from the Block Access policy.
Traveling users should inform and request access prior to their departure. A good way to do this is via Microsoft Forms:
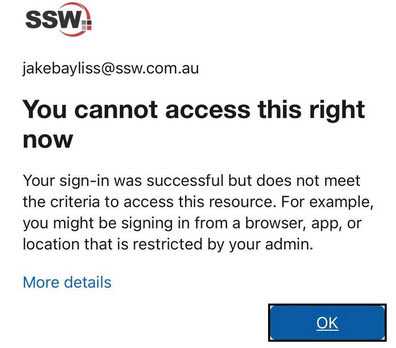
Otherwise they will get this message: